Difference between revisions of "Multi-factor authentication for Office 365"
| (13 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | [[File:O365_mfa.png |right]] | |
| − | [[File:O365_mfa.png |right | + | {{TOC_Float_Right}} |
==About this article== | ==About this article== | ||
This article includes the steps involved in configuring multi-factor authentication (MFA) for Microsoft Office 365. It is intended for all WSU students, faculty, and staff. | This article includes the steps involved in configuring multi-factor authentication (MFA) for Microsoft Office 365. It is intended for all WSU students, faculty, and staff. | ||
==What's Office 365 Multi-Factor Authentication (MFA)?== | ==What's Office 365 Multi-Factor Authentication (MFA)?== | ||
| − | In order to better protect you, your data, and our campus network from | + | In order to better protect you, your data, and our campus network from security threats, Winona State University will soon implement Multi Factor Authentication (MFA) for Office 365. Once enabled, you must also use the another verification method along with your user name and password. This adds another layer of security and significantly reduces security threats. |
| − | |||
===MFA Options=== | ===MFA Options=== | ||
| − | + | There are a variety of authentication options that can be chosen for Office 365 ranging from a verification phone call to a secret code generated by an app on your phone. Below are all of the supported options. | |
====Option 1: Smartphone Notification App==== | ====Option 1: Smartphone Notification App==== | ||
| − | This is | + | This is the easiest option if you own a smartphone. After you download and configure the '''Microsoft Authenticator''', your phone will prompt you before every login to approve the login request. After you select '''approve''' on your phone your will be logged in. |
| + | |||
| + | This method isn't for every one as users without smartphones will not be able to use this method, and if you lose your smartphone, you may temporarily lose access to your Office 365 until you go through the recovery process. | ||
====Option 2: Cell Phone Text==== | ====Option 2: Cell Phone Text==== | ||
| − | + | ||
| + | The next option is text verification. After you type in your credentials to your account, it will ask permission to send a text message to your phone. After you clock '''Send me the text''', you will receive a 6 digit code via text on your cell phone. Next you must enter this code into the field now located on the login window of your computer and you are now successfully logged into your account. | ||
| + | |||
| + | This is a great method for those without smartphones. This method is always nice because as long as your cell phone number stays the same, this method will work. This means that no extra configuration is required when you upgrade or replace your cell phone. | ||
====Option 3: Smartphone Code Generating App==== | ====Option 3: Smartphone Code Generating App==== | ||
| − | |||
| − | ====Option 4: Call My | + | The '''Microsoft Authenicator''', along with being used for option 1, can also be used for another form of authentication. This method will constantly be generating a 6 digit code every 30 seconds right on the app, that you will simply enter in office 365 after you enter your credentials. |
| − | This option | + | |
| + | This method '''does not require any data''' which means even if your are our of country with no cellular data or WiFi you can still access to your account. | ||
| + | |||
| + | ====Option 4: Call My Phone==== | ||
| + | |||
| + | This option allows you to verify via a phone call. Whenever you login, you will get an automated phone call asking you to approve the login. This method can be used with either a personal phone or an office phone, and just as in option 2, no extra configuration will be necessarily upon upgrading or replacing a phone so long as your phone number stays the same. | ||
| − | + | It is important to note that using an Office Phone as your only other verification method will disallow you from accessing your account when you do not have access to this phone. | |
| − | |||
====Option 6: University Laptop or Tablet Code Generating App==== | ====Option 6: University Laptop or Tablet Code Generating App==== | ||
| − | + | It is possible to install a code generator application on a university laptop or tablet. This will function exactly like option 3 and the '''Microsoft Authenticator'''. If you would like to setup this option, please contact {{TSC}} for more info. | |
| + | |||
| + | ====Multi-Option==== | ||
| + | All of the authentication options are better in certain situations and not so good in others. For example if you are traveling abroad and do not have access to WiFi or Cellular, the first option will not work for you. This is why we recommend setting up multiple authentication options so that no matter what situation you find yourself in, you are still able to access your Office 365 account. | ||
==Setup Trust Account== | ==Setup Trust Account== | ||
| Line 65: | Line 75: | ||
*Type in your StarID password once and click approve (or enter text option) | *Type in your StarID password once and click approve (or enter text option) | ||
| − | [[Category:Microsoft Office 365]] | + | ==More Info== |
| + | |||
| + | [https://thenextweb.com/google/2019/05/23/google-data-shows-2-factor-authentication-blocks-100-of-automated-bot-hacks/ Google data shows 2-factor authentication blocks 100% of automated bot hacks - The Next Web] | ||
| + | |||
| + | [https://heimdalsecurity.com/blog/start-using-two-factor-authentication/ Why You Should Start Using Two-Factor Authentication Now - Heimdal Security] | ||
| + | |||
| + | [https://www.wired.com/story/two-factor-authentication-apps-authy-google-authenticator/ How to Secure Your Accounts with Better Two-Factor Authentication - Wired.com] | ||
| + | |||
| + | [[Category:Security]][[Category:Microsoft Office 365]][[Category:MFA]][[Category:2FA]][[Category:Multi-Factor Authentication]] | ||
Revision as of 15:02, 16 July 2019
About this article
This article includes the steps involved in configuring multi-factor authentication (MFA) for Microsoft Office 365. It is intended for all WSU students, faculty, and staff.
What's Office 365 Multi-Factor Authentication (MFA)?
In order to better protect you, your data, and our campus network from security threats, Winona State University will soon implement Multi Factor Authentication (MFA) for Office 365. Once enabled, you must also use the another verification method along with your user name and password. This adds another layer of security and significantly reduces security threats.
MFA Options
There are a variety of authentication options that can be chosen for Office 365 ranging from a verification phone call to a secret code generated by an app on your phone. Below are all of the supported options.
Option 1: Smartphone Notification App
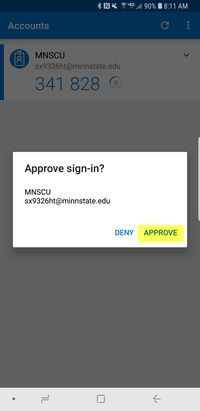
This is the easiest option if you own a smartphone. After you download and configure the Microsoft Authenticator, your phone will prompt you before every login to approve the login request. After you select approve on your phone your will be logged in.
This method isn't for every one as users without smartphones will not be able to use this method, and if you lose your smartphone, you may temporarily lose access to your Office 365 until you go through the recovery process.
Option 2: Cell Phone Text
The next option is text verification. After you type in your credentials to your account, it will ask permission to send a text message to your phone. After you clock Send me the text, you will receive a 6 digit code via text on your cell phone. Next you must enter this code into the field now located on the login window of your computer and you are now successfully logged into your account.
This is a great method for those without smartphones. This method is always nice because as long as your cell phone number stays the same, this method will work. This means that no extra configuration is required when you upgrade or replace your cell phone.
Option 3: Smartphone Code Generating App
The Microsoft Authenicator, along with being used for option 1, can also be used for another form of authentication. This method will constantly be generating a 6 digit code every 30 seconds right on the app, that you will simply enter in office 365 after you enter your credentials.
This method does not require any data which means even if your are our of country with no cellular data or WiFi you can still access to your account.
Option 4: Call My Phone
This option allows you to verify via a phone call. Whenever you login, you will get an automated phone call asking you to approve the login. This method can be used with either a personal phone or an office phone, and just as in option 2, no extra configuration will be necessarily upon upgrading or replacing a phone so long as your phone number stays the same.
It is important to note that using an Office Phone as your only other verification method will disallow you from accessing your account when you do not have access to this phone.
Option 6: University Laptop or Tablet Code Generating App
It is possible to install a code generator application on a university laptop or tablet. This will function exactly like option 3 and the Microsoft Authenticator. If you would like to setup this option, please contact Technical Support Center (TechSupport@winona.edu, 507-457-5240, Somsen Hall 207) for more info.
Multi-Option
All of the authentication options are better in certain situations and not so good in others. For example if you are traveling abroad and do not have access to WiFi or Cellular, the first option will not work for you. This is why we recommend setting up multiple authentication options so that no matter what situation you find yourself in, you are still able to access your Office 365 account.
Setup Trust Account
If you see other choices you may have set something up previously. Office 365 personal or security and privacy settings contain some of this info so it may have been added previously.
1. Go to https://account.activedirectory.windowsazure.com/Proofup.aspx
2. Sign into your account and setup MFA
Our Recommendations
- Provided you have a smart phone, we highly recommend using the Notify Me through app using the Microsoft Authenticator app as your #1 choice; followed by a backup text. This notification process makes it super easy when your account is finally tripped.
- A regular cell phone without smart capabilities use text
- If no cell phone your options are to use your office phone or use verification code from app on a university laptop.
Setup Process
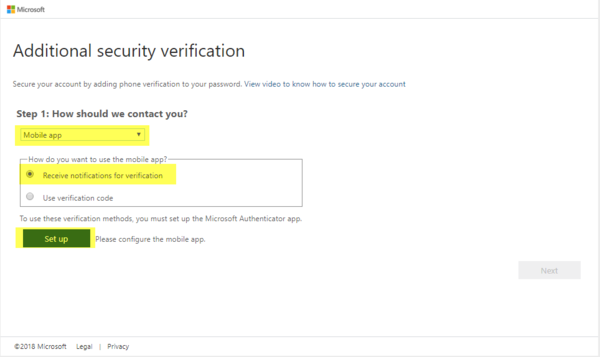
- Click on Setup
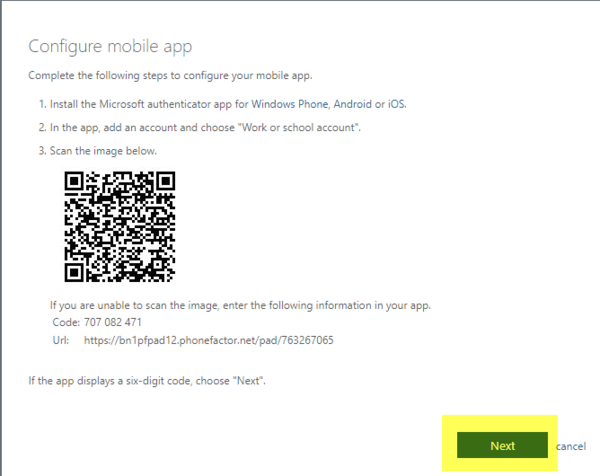
- On the next screen read through the instructions, install the app and click on Next
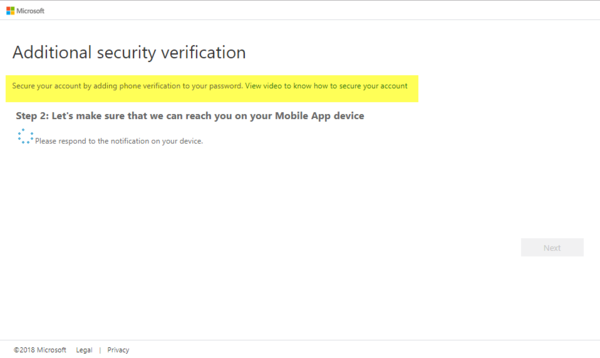
- A message will be sent to you phone
- When you get the verification message click on Approve
Activation
- Activation consists of scheduling your account to have Multifactor
- You will get a popup - Within an hour you will need to validate your account
- Type in your StarID password once and click approve (or enter text option)
More Info
Google data shows 2-factor authentication blocks 100% of automated bot hacks - The Next Web
Why You Should Start Using Two-Factor Authentication Now - Heimdal Security
How to Secure Your Accounts with Better Two-Factor Authentication - Wired.com