Difference between revisions of "Phishing"
| (30 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{{TOC_Float_Right}} | {{TOC_Float_Right}} | ||
| − | + | '''Phishing''' is the fraudulent attempt to obtain sensitive information (e.g., usernames, passwords, credit card details) via email, text messages, and telephone communication by disguising oneself as a trustworthy entity. Numerous phishing emails are sent to WSU addresses every day. Many are detected and deleted before they reach your mailbox, but some cleverly disguised messages get through. Falling for phishing schemes can have terrible consequences for you and puts the entire {{WSU}} community at risk. Using your credentials and associated permissions, attackers can access {{WSU}} network resources and data, including private information to which you have access. Protecting {{WSU}} from phishing attacks is everyone's responsibility and an important part of being a good digital citizen. Your best defenses against phishing are knowledge, vigilance, and [[Multi-factor authentication for Office 365|multi-factor authentication]]. | |
| − | '''Phishing''' is the fraudulent attempt to obtain sensitive information (e.g., usernames, passwords, credit card details) via email, text | ||
==What everyone should know== | ==What everyone should know== | ||
===Phishing fundamentals=== | ===Phishing fundamentals=== | ||
| − | |||
#'''Always enable multi-factor authentication''' on any account that offers it. [[Multi-factor authentication for Office 365|Learn more...]] | #'''Always enable multi-factor authentication''' on any account that offers it. [[Multi-factor authentication for Office 365|Learn more...]] | ||
#'''Always suspect''' any request for your password, social security number, or any other private data via email or phone. | #'''Always suspect''' any request for your password, social security number, or any other private data via email or phone. | ||
| − | #'''Never respond''' to a suspicious message or engage the attacker in any way. | + | #'''Never respond''' to a suspicious message or engage the suspected attacker in any way. |
#'''Never select''' a link in any suspicious email or text message. | #'''Never select''' a link in any suspicious email or text message. | ||
#'''Never forward''' suspicious email to others, even {{WSU}} technical support staff. | #'''Never forward''' suspicious email to others, even {{WSU}} technical support staff. | ||
| Line 15: | Line 13: | ||
===Reporting suspected phishing=== | ===Reporting suspected phishing=== | ||
====Suspicious Outlook email messages==== | ====Suspicious Outlook email messages==== | ||
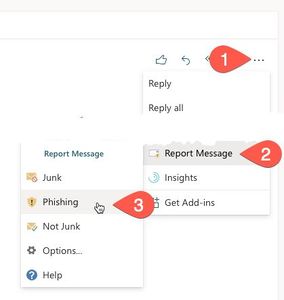
| − | *In the online version of Outlook, select '''Report Message...Phishing''' from the '''More actions''' menu while viewing the message | + | *In the online version of Outlook, select '''Report Message...Phishing''' from the '''More actions''' menu while viewing the message (Fig 1) |
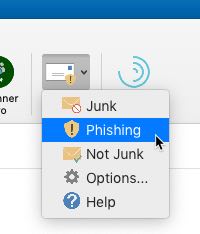
| − | *In the installed, desktop version of Outlook, select '''Phishing''' from the '''Report Message''' menu on the Home ribbon while viewing the message | + | *In the installed, desktop version of Outlook, select '''Phishing''' from the '''Report Message''' menu on the Home ribbon while viewing the message (Fig 2) |
| − | |||
====Suspicious text messages, phone calls, and voicemail messages==== | ====Suspicious text messages, phone calls, and voicemail messages==== | ||
*Send an email to [mailto:abuse@winona.edu abuse@winona.edu] describing the message | *Send an email to [mailto:abuse@winona.edu abuse@winona.edu] describing the message | ||
| + | ====Screenshots==== | ||
| + | <gallery widths=300px heights=300px> | ||
| + | File:Phishing report outlook online.jpg|Fig 1: In Outlook online, select More actions (1), Report Message (2), Phishing (3) | ||
| + | File:Phishing report outlook desktop.jpg|Fig 2: In Outlook desktop, select Report Message...Phishing | ||
| + | </gallery> | ||
| + | ===If you get phished=== | ||
| + | #Contact the {{TSC}} immediately | ||
| + | #Change the passwords on all potentially affected accounts immediately | ||
===Types of phishing messages=== | ===Types of phishing messages=== | ||
| Line 29: | Line 34: | ||
*'''Vishing''' - Voice messages (e.g., phone calls, voicemail messages) used to increase the perceived urgency and authenticity of the attack | *'''Vishing''' - Voice messages (e.g., phone calls, voicemail messages) used to increase the perceived urgency and authenticity of the attack | ||
| − | ==Stay vigilant== | + | ==Stay vigilant and safe== |
| − | Here are some good tips for spotting possible phishing messages: | + | Here are some good tips for spotting possible phishing messages and protecting yourself from attack: |
| + | *Enable multi-factor authentication on any account that offers it. Once enabled, even if attackers steal your password, they cannot access your account without a second form of verification. | ||
*No one from any Minnesota State organization will ever ask for any private data (e.g., your password, social security number) via phone, email, or text. | *No one from any Minnesota State organization will ever ask for any private data (e.g., your password, social security number) via phone, email, or text. | ||
| − | *Be wary messages from people or organizations you don't know and messages from those you do know, but that | + | *Be wary of messages from people or organizations you don't know and messages from those you do know, but that include unusual requests (e.g., purchase gift cards for family members). |
| − | * | + | *Phishing messages often include typos, spelling errors, and grammatical mistakes. |
*Phishing messages often convey a heightened sense of urgency or importance (e.g., a limited time to reply, severe negative consequences). | *Phishing messages often convey a heightened sense of urgency or importance (e.g., a limited time to reply, severe negative consequences). | ||
| − | *Be suspicious of any email or text message that | + | *Be suspicious of any email or text message that asks you to select a link or web address embedded in the message. Mouse over the link without selecting it to examine the web address or URL. If the address looks unusual in any way, report it. |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
{{#widget:YouTube|id=fFNZYio5x68}} | {{#widget:YouTube|id=fFNZYio5x68}} | ||
| − | == | + | ==More information== |
| − | + | *[[Multi-factor authentication for Office 365]] | |
| + | *[http://en.wikipedia.org/wiki/Phishing Phishing as defined by Wikipedia] | ||
*[[Student Safe Computing]] | *[[Student Safe Computing]] | ||
*[[Private Data Protection]] | *[[Private Data Protection]] | ||
| Line 57: | Line 54: | ||
*[https://www.stopthinkconnect.org/ Online Safety Awareness site "Stop.Think.Connect"] | *[https://www.stopthinkconnect.org/ Online Safety Awareness site "Stop.Think.Connect"] | ||
| − | [[ | + | [[Category:Security]][[Category:Microsoft Office 365]][[Category:MFA]] |
Revision as of 20:14, 6 February 2020
Phishing is the fraudulent attempt to obtain sensitive information (e.g., usernames, passwords, credit card details) via email, text messages, and telephone communication by disguising oneself as a trustworthy entity. Numerous phishing emails are sent to WSU addresses every day. Many are detected and deleted before they reach your mailbox, but some cleverly disguised messages get through. Falling for phishing schemes can have terrible consequences for you and puts the entire Winona State University community at risk. Using your credentials and associated permissions, attackers can access Winona State University network resources and data, including private information to which you have access. Protecting Winona State University from phishing attacks is everyone's responsibility and an important part of being a good digital citizen. Your best defenses against phishing are knowledge, vigilance, and multi-factor authentication.
What everyone should know
Phishing fundamentals
- Always enable multi-factor authentication on any account that offers it. Learn more...
- Always suspect any request for your password, social security number, or any other private data via email or phone.
- Never respond to a suspicious message or engage the suspected attacker in any way.
- Never select a link in any suspicious email or text message.
- Never forward suspicious email to others, even Winona State University technical support staff.
- Always report any suspicious messages using the procedures listed below.
Reporting suspected phishing
Suspicious Outlook email messages
- In the online version of Outlook, select Report Message...Phishing from the More actions menu while viewing the message (Fig 1)
- In the installed, desktop version of Outlook, select Phishing from the Report Message menu on the Home ribbon while viewing the message (Fig 2)
Suspicious text messages, phone calls, and voicemail messages
- Send an email to abuse@winona.edu describing the message
Screenshots
If you get phished
- Contact the Technical Support Center (TechSupport@winona.edu, 507-457-5240, Somsen Hall 207) immediately
- Change the passwords on all potentially affected accounts immediately
Types of phishing messages
Familiarize yourself with the the types of phishing messages attackers use to trick you. Perhaps the most convincing are messages targeting you directly based on information about you the attacker found online. Fraudulent messages in which the attacker actually speaks to you over the phone can also be difficult to detect.
- Basic phishing - Generic messages sent to a large number of people in hopes that some will fall victim
- Spear phishing - Personalized messages targeting you directly based on the attacker's knowledge about you (e.g., in what area of Winona State University you work, coworkers' names), usually obtained from public, online sources
- Whaling - Personalized messages targeting high-value targets (e.g., people with access to valuable data) directly
- Cat phishing - Personalized messages targeting you directly that attempt to establish an interpersonal relationship with you for future exploitation
- Vishing - Voice messages (e.g., phone calls, voicemail messages) used to increase the perceived urgency and authenticity of the attack
Stay vigilant and safe
Here are some good tips for spotting possible phishing messages and protecting yourself from attack:
- Enable multi-factor authentication on any account that offers it. Once enabled, even if attackers steal your password, they cannot access your account without a second form of verification.
- No one from any Minnesota State organization will ever ask for any private data (e.g., your password, social security number) via phone, email, or text.
- Be wary of messages from people or organizations you don't know and messages from those you do know, but that include unusual requests (e.g., purchase gift cards for family members).
- Phishing messages often include typos, spelling errors, and grammatical mistakes.
- Phishing messages often convey a heightened sense of urgency or importance (e.g., a limited time to reply, severe negative consequences).
- Be suspicious of any email or text message that asks you to select a link or web address embedded in the message. Mouse over the link without selecting it to examine the web address or URL. If the address looks unusual in any way, report it.